3 Essential Components to Build into Your Incident Response Program in 2017
[vc_row css=”.vc_custom_1452687555475{margin-bottom: 100px !important;}”][vc_column offset=”vc_col-lg-9 vc_col-md-9″ css=”.vc_custom_1452702342137{padding-right: 45px !important;}”][vc_custom_heading source=”post_title” use_theme_fonts=”yes” el_class=”no_stripe”][stm_post_details][vc_column_text css=”.vc_custom_1487449721337{margin-bottom: 20px !important;}” el_class=”no_stripe”]
In my previous role as a network security architect at a Fortune 500 company, I worked on a team of two. This required us to wear a number of hats. One of our core operating functions was performing incident response across 70,000 endpoints globally. Initially, our program was very reactive. Over the course of a year, we began maturing the program by adding three components: key metrics and reporting, a process of continuous improvement and tuning, and alert prioritization. These components helped us to take control of our response program, provide insight to upper management on the program’s efficiency and responsiveness, and gain visibility into our return on security investment (ROSI).
You, the security professional, are the single most valuable security investment that your company will make. Investments in technology are meaningless if the organization lacks skilled personnel and process to prioritize, validate, and respond to potential security events. Thus, it is critical that you figure out an approach that allows you to use your time effectively and maximize your response bandwidth. The following three components are a great starting point for organizations looking to mature their response program.
Component 1: Metrics
We all love them. Metrics allow us to measure progress. Metrics help us identify areas for improvement. I would strongly encourage every organization to take a day or two (because security professionals have so much free time) to identify the metrics that will help you track your program’s effectiveness.
- How many alerts did my tooling generate in the last month?
- How many incidents did I respond to last month?
- From which detection methods—data sources, products, or services—did these incidents materialize?
- Which tools are providing the highest fidelity alerts (based on conversions to incidents)?
- How much time did I spend acknowledging, confirming, and remediating threats?
- How can I gauge product efficacy and improvement—out of box alerts compared against tuned alerts over time?
These metrics gave us very deep insight into our response operations and allowed us to address key areas that we needed to improve. If you do not have a system in place to report on these metrics (or something similar), this should be your first priority. You cannot accurately assess your IR program’s performance without these pieces of information.
Component 2: Continuous Improvement and Product Tuning
Tuning products is a continuous cycle of alerting, responding, tuning, and monitoring. It would be a generous industry if we only had to turn a product on and respond to high fidelity events all day, however that is typically not the case.
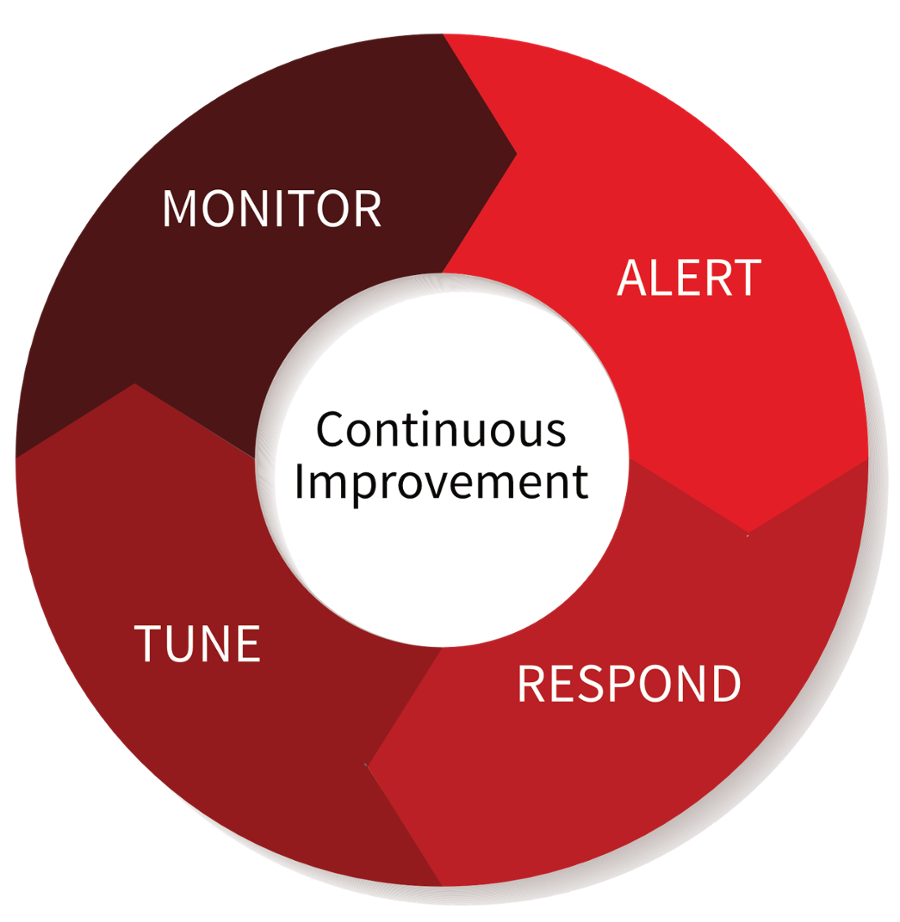 Every product produces noise as each environment is different from the next. As a security professional you have to be able to weed through the false positives quickly and get to the high fidelity events quickly. How do you effectively get to a place of receiving high fidelity alerts? It may sound cliché, but it’s true: what you put into a product is what you will get out of it. We found at times we would receive an enormous number of alerts and turn it off because of it. Yes, I admit it. We would stop alerting on a product that flooded our email with alerts. However, we would analyze the data being produced by it to understand why so that we could properly tune it and continue to monitor. Eventually, this cycle led us to create properly tuned correlation rules that generated high fidelity and actionable alerts.
Every product produces noise as each environment is different from the next. As a security professional you have to be able to weed through the false positives quickly and get to the high fidelity events quickly. How do you effectively get to a place of receiving high fidelity alerts? It may sound cliché, but it’s true: what you put into a product is what you will get out of it. We found at times we would receive an enormous number of alerts and turn it off because of it. Yes, I admit it. We would stop alerting on a product that flooded our email with alerts. However, we would analyze the data being produced by it to understand why so that we could properly tune it and continue to monitor. Eventually, this cycle led us to create properly tuned correlation rules that generated high fidelity and actionable alerts.
Component 3: Prioritization
The more tools an environment has, the more need for alert prioritization across your tooling. One of the best ways we identified for prioritizing events was to add as much business context to the data as possible. For instance, focus on the most critical places where data resides first and work outward from there. Critical network ranges that housed confidential or intellectual property would receive highest priority, due to business impact, from any product to ensure that we focused priority items first. We would then add the human business context; C-levels, HR department, R&D managers, and marketing directors are all high-value targets and should have a higher priority for an investigation. Additionally, understanding holistically how widespread an event is can drive the impact from low to high.
The three components outlined above provide a solid framework that can help solve the biggest challenges security professionals face when organizing their IR programs. To walk through these areas in deeper detail, watch our on-demand webinar where I presented alongside security professionals who led operations at Motorola Solutions, OfficeMax, and Heroku. You’ll have an opportunity to hear what key metrics your peers are reporting on, as well as more information on how they prioritize alerts and tune their tooling.
Source: redcanary.com
[/vc_column_text][stm_post_bottom][/vc_column][vc_column width=”1/4″ offset=”vc_hidden-sm vc_hidden-xs”][stm_sidebar sidebar=”527″][/vc_column][/vc_row]







