SWIFT Customer Security Controls Framework Assessment
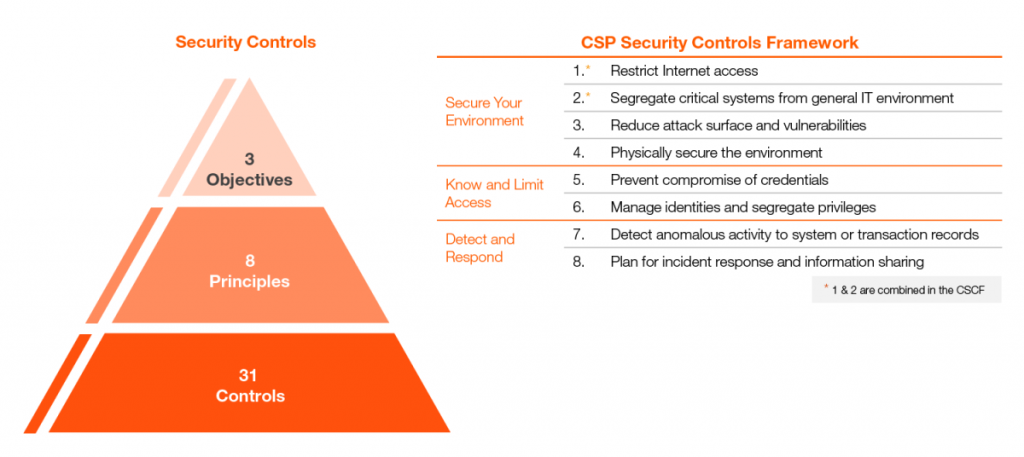
The SWIFT Customer Security Controls Framework (CSCF) consists of both mandatory and advisory security controls for users in the SWIFT community. The controls will evolve over time to combat new and emerging threats and implement new safeguards to reduce cybersecurity risk.
ABOUT SWIFT CSP
What is the SWIFT CSP?
Reinforcing the Security of the Global Financial System
The mandatory security controls establish a security baseline for the entire community. They must be implemented by all users on their local SWIFT infrastructure. SWIFT has chosen to prioritize these mandatory controls to set a realistic goal for near-term, tangible security gains and risk reduction. The advisory controls are based on recommended practice that SWIFT recommends all users to implement. Over time, controls may change due to the evolving threat landscape, the introduction of new technologies, the evolution of security-related regulations in major jurisdictions, developments in cybersecurity practices, or user feedback.
Security Attestation
You are making cross border transactions, so the security of your local SWIFT environment impacts the overall global financial system. The potential impact of a correspondent bank cutting ties with a local commercial bank through “de-risking” measures could mean that business goes down, and bigger players dominate the market. As part of the Customer Security Programme (CSP), every SWIFT user must submit an annual Security Attestation, showing compliance levels with the controls.
Increasing transparency in the SWIFT user community
Submit an attestation annually
All users have to attest before the expiry date of the current controls version, confirming full compliance with the mandatory security controls no later than 31st December, and must re-attest at least annually thereafter. Re-attestation has to be done between July and December each year. New joiners need to attest before going live on the SWIFT network. Security Attestations have to be submitted via the KYC-Security Attestation application (KYC-SA). A new version of the controls becomes available in the application each year in early July. A detailed description of the security attestation process and requirements is available in the SWIFT Customer Security Controls Policy.
What happens if I don’t submit my attestation?
SWIFT reserves the right to report users that have not attested compliance with all mandatory security controls (or that connect through a non-compliant service provider) to their local supervisors.
You are in breach of the policy if:
- you don’t have a valid attestation: you either did not submit an attestation, or your attestation is expired
- you are not compliant with the mandatory controls
- you connect through a non-compliant service provider
- you did not complete a SWIFT mandated external assessment
How can we help?
Cybercriminals are deploying increasingly sophisticated means of circumventing individual controls within organisations local SWIFT environments and probed further into their systems to execute well-planned and finely orchestrated attacks. The determination, patience and cunning the attackers are demonstrating makes it more imperative now more than ever that customers rapidly deploy and maintain all basic cyber hygiene tools and measures, comprehensively adhere to recommended security controls, and incorporate all the elements set out in SWIFT’s Customer Security Programme in their local SWIFT environments and extend these security control requirements to the general IT enterprise.
We are listed in the Directory of CSP assessment providers. We use our collective experience in cyber defense and in-depth knowledge of the SWIFT Customer Security Controls Framework to contribute to evaluating the risks drivers associated with the SWIFT controls. Our battle-tested SWIFT CSP assessors will guide and assist you in the remediation of non-conformities discovered during the assessment. They will work with you to perform a cybersecurity assessment of your SWIFT-related environment by reviewing, scoping and conducting a gap analysis leading to attestation of compliance with the SWIFT Customer Security Controls Framework. These control mechanisms must be of the same level in the entire end-to-end chain of the transaction lifecycle as any vulnerability in your SWIFT network and application infrastructure will be the weakest link in the security implementation framework.
The security of your organization is our business
Phone Number(s)
🇬🇭 +233 (0) 243 335 025
🇬🇭 +233 (0) 55 652 6210
🇬🇭 +233 (0) 243 335 025 ( )
)
Email Address
info@globalsecuresolutions.com
Local Address
H/No. 17 Peter Ala Adjetey Avenue, North Labone, Accra – Ghana.




